|
View the full video
|
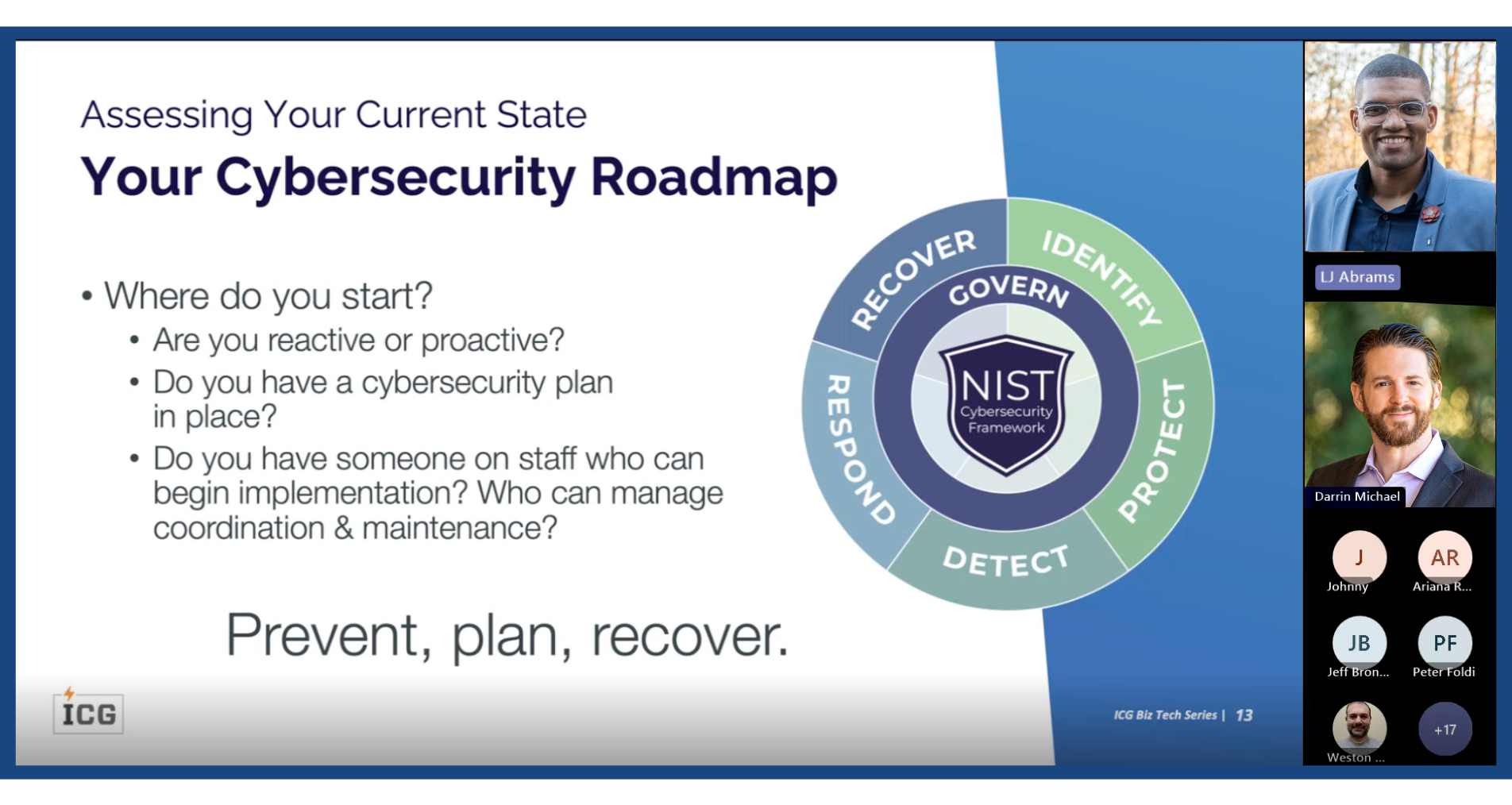
Our recent Cybersecurity Webinar tackled key questions every business must ask itself to evaluate its defenses against the growing threat of cybercrime. |
|
|
|
Are you relying solely on built-in software to protect your company? |
|
|
|
How would your organization respond if your systems were compromised? Can you afford serious downtime? |
|
|
|
Are you allocating enough resources—time, staff, or budget—to ensure your cybersecurity best practices are robust enough? |
|
A Multi-Layered Cybersecurity Approach:The session emphasized that a multi-layered cybersecurity approach is no longer a luxury but a necessity. Traditional tools like anti-malware software alone are insufficient against increasingly advanced threats like ransomware, phishing, and AI powered cyberattacks. We provided real-world attack examples and discussed how a system failure or data breach can severely disrupt business operations, affect customer trust, and damage your company’s reputation. One of the key issues addressed was resource allocation in cybersecurity. Many organizations, especially SMBs, face challenges when it comes to dedicating the necessary time, staff, and budget to cybersecurity. However, our experts shared actionable strategies for maximizing resources—prioritizing high-risk areas, leveraging automation, and ensuring your team remains educated on the latest cyber threats for businesses. |
|
Top Questions from the Webinar:
|
How do I know if my company has a deficit of talent in cybersecurity? |
|
|
If you don't have someone on your team who can both architect and execute a solid cybersecurity plan, and if your team can’t demonstrate a comprehensive strategy, then the answer is likely "yes, you have a deficit". Can you assess your cybersecurity posture? Being proactive is key to preventing breaches, not waiting to react once one happens. If you're not confident in your ability to assess and strengthen your cybersecurity, it's time to address that talent gap. |
|
|
Can you explain Zero Trust Policy? |
|
|
Zero Trust is a cybersecurity framework that requires verification of every user, device, and application before granting access to the network. You don't trust any user until they verify their identity; tools like multi-factor authentication (MFA) and security tokens are used to ensure identity verification. It also applies least-privilege access, meaning users can only access what they need to perform their job. Every application connecting to the network must authenticate each time, ensuring constant security. |
|
|
Is there a solution for recovery after paying a ransom but not getting your data back? |
|
|
Honestly, you have to cross your fingers and pray. Unfortunately, there is no guarantee your data will be recovered even with a third-party forensic expert, and it won't be quick or cheap. Believe me, an ounce of prevention is worth so much more than remediation on the backend. The real solution is prevention through robust backups. A 3-2-1 backup plan—three copies of your data on two types of media, with one offsite—makes your data nearly untouchable, ensuring full recovery if disaster strikes. Prevention is always better than costly remediation. |
|
|
What about Penetration Testing? |
|
|
Penetration Testing involves hiring a white hat hacker team to test your network security by attempting to breach it. They identify vulnerabilities by seeing how far they can penetrate your system. This gives you a clear, solid understanding of your security weaknesses and where you need to improve. |
|
|
Why should you trust an MSP for cybersecurity over a big software company? |
|
|
Big brands treat you like a number, lack familiarity with your systems, and only offer billable solutions. In contrast, process-focused MSPs like us at ICG understand your business processes, infrastructure, and platform requirements. We provide tailored cybersecurity, combining training, software, and expertise to keep you secure and recoverable, ensuring you’re not reliant on offshore resources or limited by impersonal service. |
Strategies to Defend Against Cyberattacks:
|
The webinar also outlined effective best practices to defend against cyberattacks, with a focus on: |
In addition, we highlighted tools that help maintain compliance in cybersecurity and ensure business continuity during cyberattacks: |
|
|
|
Wrapping Up... Prevent Cybersecurity Breaches:
In conclusion, our webinar emphasized that cybersecurity is an ongoing investment. It’s not just about meeting compliance requirements but about ensuring the safety, trust, and operational continuity of your business in the face of increasingly sophisticated cybercriminal tactics. By staying informed, prepared, and proactive, businesses can prevent cybersecurity breaches, safeguard their data, protect their reputation, and minimize the impact of advanced cyberattacks.
Stay protected. Stay prepared.
Check out our Biz Tech Webinar Series on our Upcoming Events page!

 (2).png)