Discover the Power of Cybersecurity Protection.
|
With the right software, service, support, and remediation combination, ICG offers next-generation cybersecurity and anti-intrusion solutions to secure your digital assets and sensitive information. We transform your IT infrastructure into a fortress. |
|
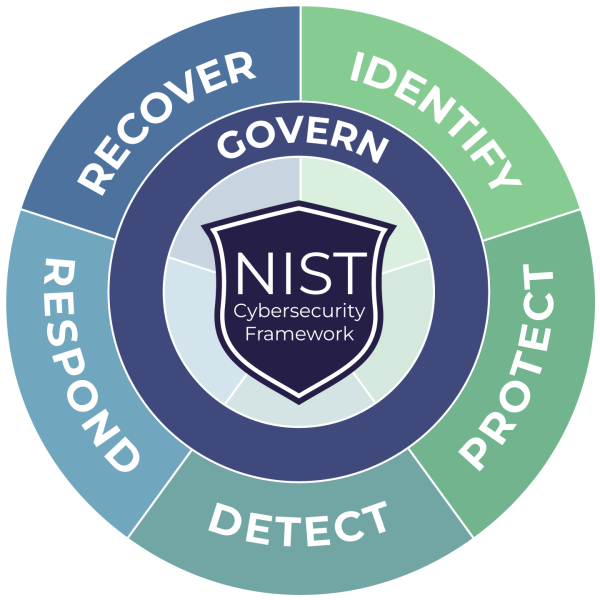
Cybersecurity has become one of the most pressing threats an organization can face, where poor cybersecurity can lead to operational disruptions, regulatory enforcement, lost sales, a tarnished corporate reputation, and much other trouble. But don't worry, ICG is here to help. We emphasize vigilance, not fear. Our Approach: ICG follows the only proven strategy for creating an effective cybersecurity risk management program that avoids all missteps. We use the NIST Cybersecurity Framework from the most trusted source. Beginning with proven NIST compliance and adding ICG's decades of expertise and foundational approach, we build the best, most effective cybersecurity program for your organization. |
 |
|
|
|
|
|
|
Why Choose ICG |
||||||
|
|
ICG offers a range of state-of-the-art cybersecurity and anti-malware solutions to secure your digital assets and sensitive information. We provide cost-effective solutions that are scalable, easily administered, and provide operational excellence, all while being monitored 24/7/365 by our vigilant SOC. You can focus on your business activities without worrying about the complexities of protecting all aspects of your organization. The factors that make ICG steps above all other third-party providers are: |
|||||
|
|
|||||
An Undisputed Leader in Cybersecurity
Any way you cut it, ICG is #1.
| Our lightning-fast detection and remediation time is due to a careful combination of process, methodology, experience, and the right tools, ensuring your shields are always up. Our vast expertise comes from many avenues, such as being part owner and an integral part of the collective of Managed Services Collective. |
|
Average Time-to-Detect |
Average Time-to-Investigate |
Average Time-to-Remediate |

Interested in reading more about Response and Detection averages, click here.
Protecting Companies of All Sizes, from the SMB to the Enterprise.ICG's superior response time is a key differentiator. We offer solutions that prevent, protect, and remediate incidents and provide actionable insights to correct and prevent future incidents. |
||
|
|
Our security operations center never rests. Trust us to find and fix your company's vulnerabilities.
Cybersecurity Offerings from ICG
 |
INTRODUCINGICG Endpoint CompleteICG is a proud co-owner of Endpoint Complete, a cybersecurity company that provides complete data protection services. Together, we focus on security software and services designed to deliver enterprise-level security and compliance without the enterprise-level price. Our team of professionals provides year-round operations that monitor, prevent, detect, and hunt threats to your business. Combining that with our assessments, pen testing, and training programs ensures our customers' peace of mind, as they can expect excellent planning, superior incident handling, immediate remediation, rollback, recovery, and more.
|
Security Operations Center (SOC)Our managed Security Operations Center (SOC) team monitors, detects, investigates, and escalates threats 24/7. Gain access to years of security experience and expertise without the burden of maintaining an in-house security team and infrastructure. We take pride in our cyber expertise, commitment to excellence, and dedication to delivering innovative SOC-managed services. Our track record of success is not only reflected in the satisfaction of our clients but also in the recognition we've received from industry-leading organizations.
|
|
Cybersecurity Online TrainingGet the Cybersecurity Online Training your company needs. Every company has unique requirements and challenges regarding security training. We start with an in-depth review to fully understand exactly what you do (and don't) need. A common myth is that cybersecurity only involves digital solutions. The truth is that most successful cyberattacks result from human error or oversight. Phishing attempts are the largest source of successful cyberattacks. Learn how to identify and avoid falling for these attacks properly. Your team already has much to keep track of when doing their jobs. We tailor our training specific to your organization to maximize impact and reduce effort.
|
|
Advanced Email SecurityPhishing is the single most common form of cybercrime. Cybercriminals send an estimated 3.4 billion emails a day designed to look like they come from trusted senders, or over a trillion phishing emails per year. For enterprises, the average cost of a ransomware attack, including downtime and remediation, is estimated at ~$1,500,000. These numbers demand the strongest possible email protection. ICG has partnered with one of the leading email security platforms to ensure you are one step ahead of threats. Our cutting-edge offerings offer proactive threat detection, brand protection, awareness training, and data retention features essential for today's dynamic workplaces. Our solutions are crafted to revolutionize email and security, serving as vigilant guardians for organizations.
|
|
Cybersecurity Assessment / Health CheckA Cybersecurity Assessment evaluates the security posture of an organization's information systems, networks, and assets. It involves identifying the threats, vulnerabilities, and risks that could compromise the data and services' confidentiality, integrity, and availability. A Cybersecurity Health Check is a type of cybersecurity assessment that provides a quick and comprehensive overview of an organization's current state of cybersecurity. It can help an organization identify the most critical and urgent security issues and gaps and provide recommendations for improvement.
|
|
Cybersecurity Compliance Audit / AssistanceA Cybersecurity Compliance Audit is a systematic and independent examination of the business's cybersecurity policies, procedures, and practices. It aims to evaluate the extent to which the business complies with applicable laws, relevant standards, regulations, guidelines, and best practices and to identify any gaps, weaknesses, or deficiencies that may pose risks to the confidentiality, integrity, and availability of the information systems and assets. ICG has decades of experience in multiple sectors, guaranteeing best industry practices and compliance in NIST (National Institute of Standards and Technology), HIPAA (Health Insurance Portability and Accountability Act), PCI Security Standards (Payment Card Industry), FDA (Food and Drug Administration), GCA (Grand and Contract Accounting), and FedRAMP (Federal Risk and Authorization Management Program). |
|
Cybersecurity Planning and Implementation ServicesAt ICG, we are committed to ensuring that your cybersecurity plan instills complete confidence. We carefully determine the most effective, secure, and compliant measures to create the most robust security posture and fully safeguard your company's data, assets, and personnel. We then seamlessly implement these measures with minimal disruptions to day-to-day operations. |
Stop Threats that Evade Traditional FirewallsPut the best Cybersecurity Solutions to work for your company. ICG takes cybersecurity beyond firewalls, providing a comprehensive suite of cybersecurity solutions required to stay proactive in today's ever-evolving threat landscape. |
||
|
|
___________
Our Top Recommendations
“The New Nine”
|
Starting a cybersecurity journey can be daunting, yet it's crucial. To aid in this process, we've outlined nine essential steps, known as ICG's 'New Nine', to significantly bolster your security measures and reduce the risk of breaches or compromises. These steps are vital as companies navigate the aftermath of the pandemic and the shift towards remote work. |
|
Develop a Security Team The team should include management along with IT and is responsible for implementing security measures, monitoring suspicious activity, and being able to take immediate action against cyber threats. |
Purchase Cybersecurity Insurance We don't have a preferred vendor, but cybersecurity insurance is very important. To guarantee a payout in the event of an incident, be sure your policy is paid and up-to-date without any lapses in coverage. |
Filter, Archive, and Back Up Email We recommend ICG Mimecast for cloud-based email management of Microsoft email products. It provides security, archiving, and continuity services for business email. |
|
Secure and Monitor the Perimeter of All Locations A next-generation firewall offers web content filtering and anti-malware. It can detect and block sophisticated attacks by enforcing security policies at the application, port, and protocol levels. |
Stay Compliant Organizations must achieve compliance by establishing risk-based controls that protect information confidentiality, integrity, and availability; falling behind will weaken your boundaries. |
System Administration, Patching, and Upgrading Utilize a security platform like Endpoint Complete to provide a proven mix of software, services, remediation, and corrective actionable insights to prevent future outbreaks. |
|
Secure and Monitor Endpoint Devices Ensure all connected devices have security precautions to ensure each device is an asset rather than a liability. |
Backups and a Disaster Recovery Plan Run daily immutable backups and ensure a disaster recovery plan is in place and is actionable if/when an unplanned incident occurs. |
Implement Password Management Ultizing a multifactor authentication system reduces the risk of account takeovers and provides additional security for users and their accounts. |
___________
ICG offers a complete cybersecurity solution and a host of professional services to fit the needs of businesses of all sizes.
Contact us today for more information or download the ICG Cybersecurity Product Sheet.